Dashi USM™
Security Operations meets Information Security Management.
Dashi USM™ delivers security to organizations of all shapes and sizes.
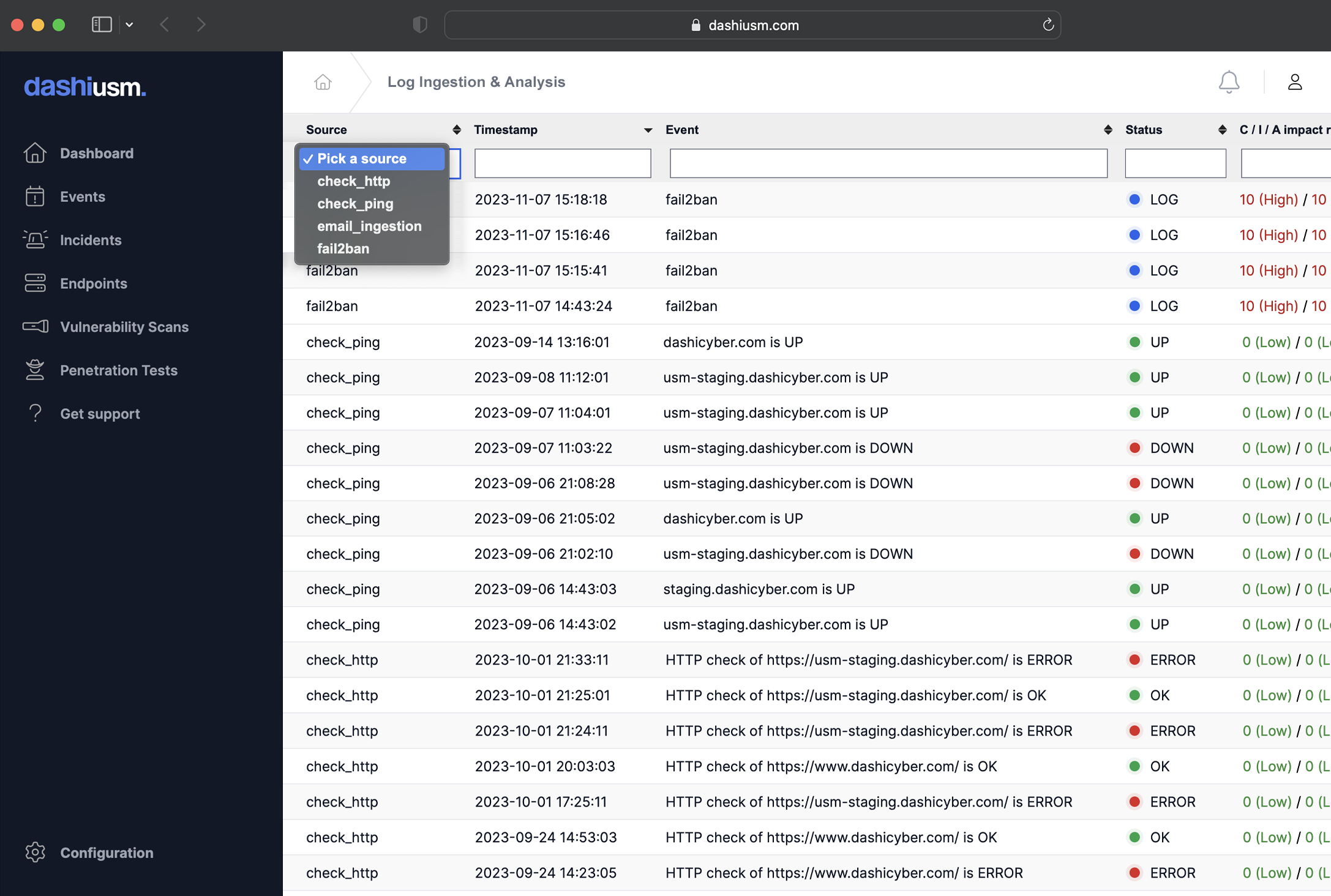
Dashi USM™ includes powerful scanning tools to detect and notify you about unauthorized changes, known vulnerabilities, misconfigured servers, unresponsive websites and more. In addition to the built-in scanners, Dashi USM™ easily integrates with your existing tools via email ingestion or a simple API to centralize event management.
Powerful tools
to help you identify and manage security risks
Making sense out of the noise is hard. Dashi USM™ automatically cross-links events to risks, endpoints, information assets, vulnerability scans, port scans, recurring events, and more. This allows you to quickly identify and manage security risks.
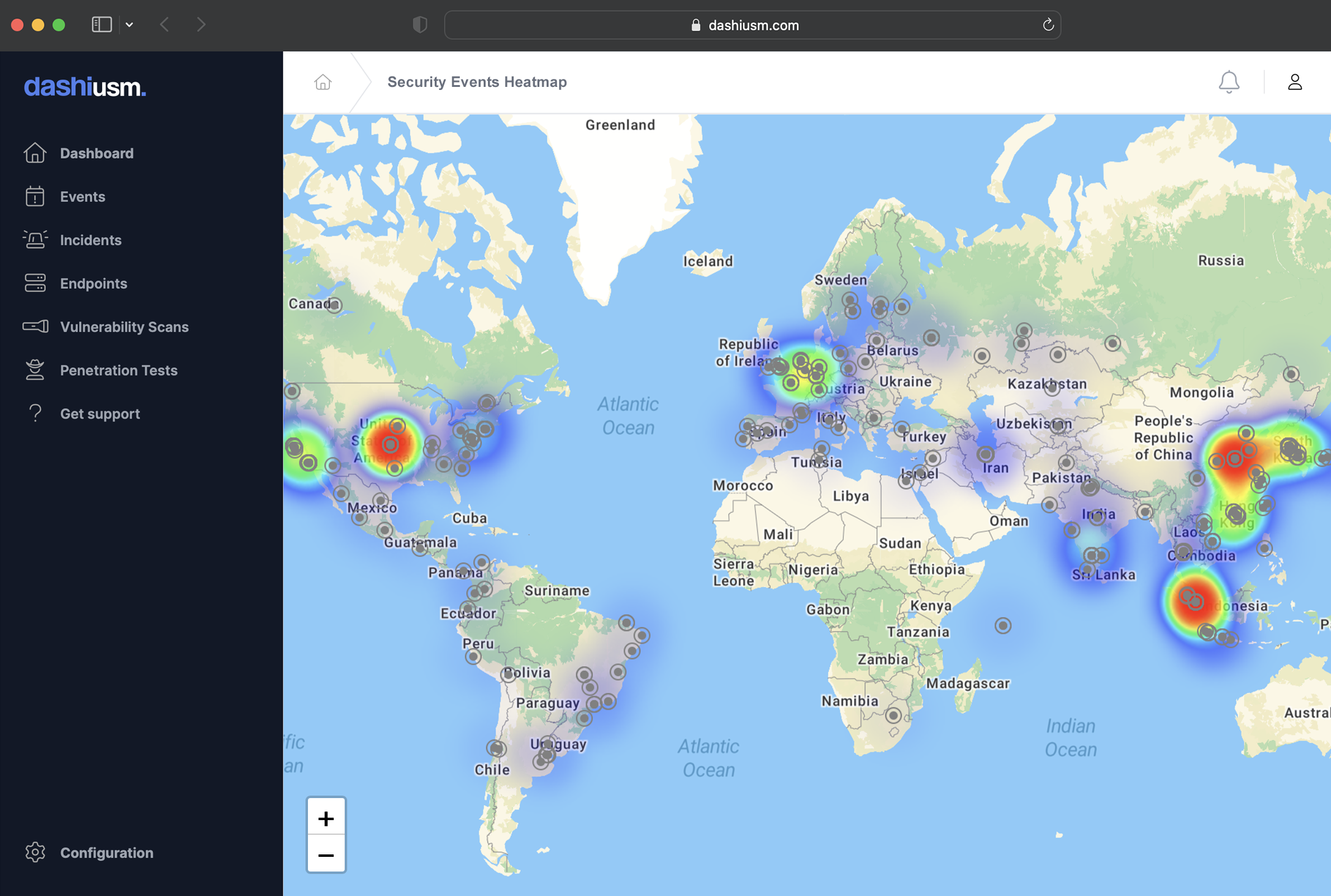
Monitor open ports
Know your attack surface
Dashi USM™ scans your endpoints for open ports and services. A dynamic port <-> endpoint map enables visualization of your network. Tabular views help identify ports that are open but should be closed. Alerts notify you every time a port is opened or closed, providing a key indicator of failed services or potential back doors.
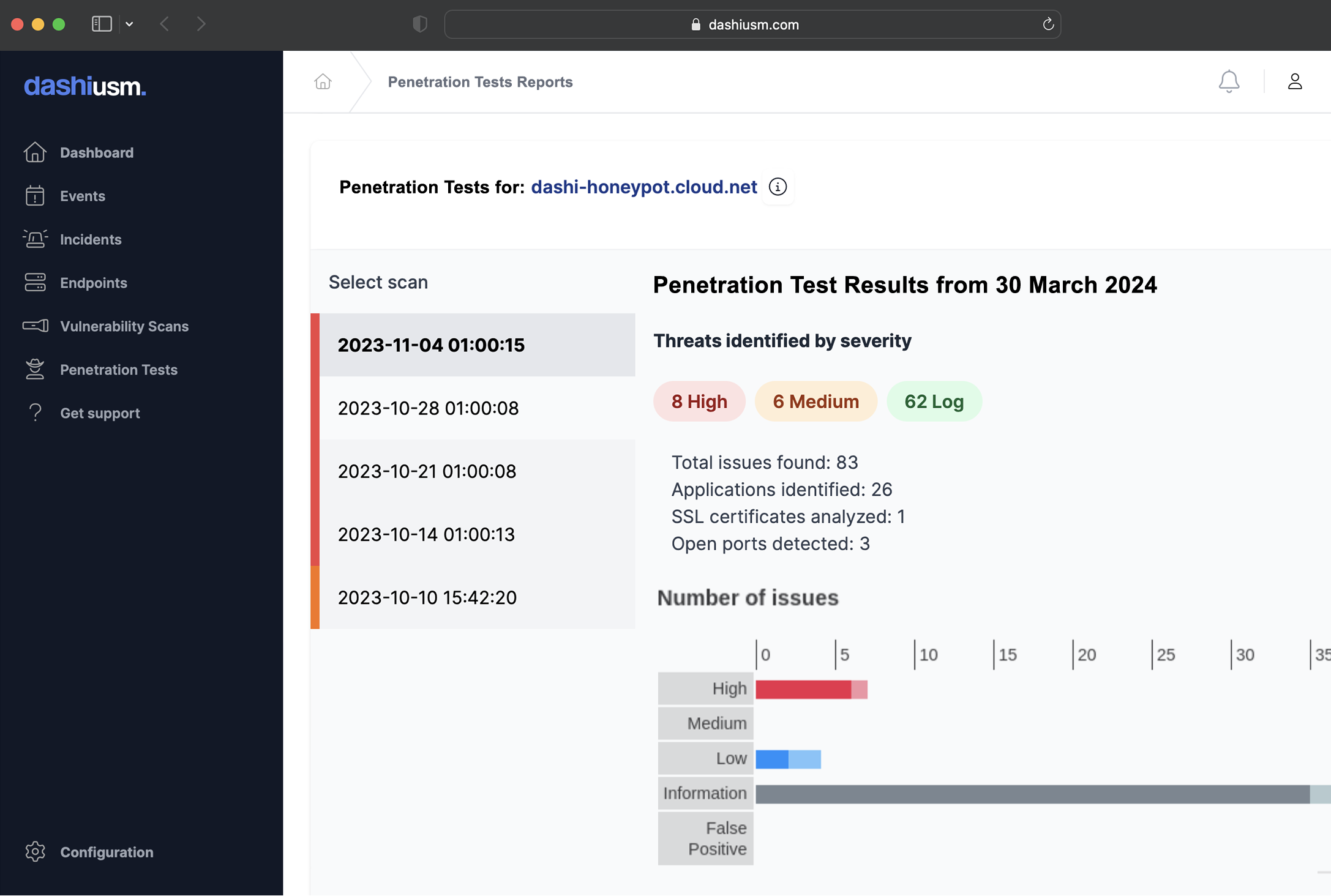
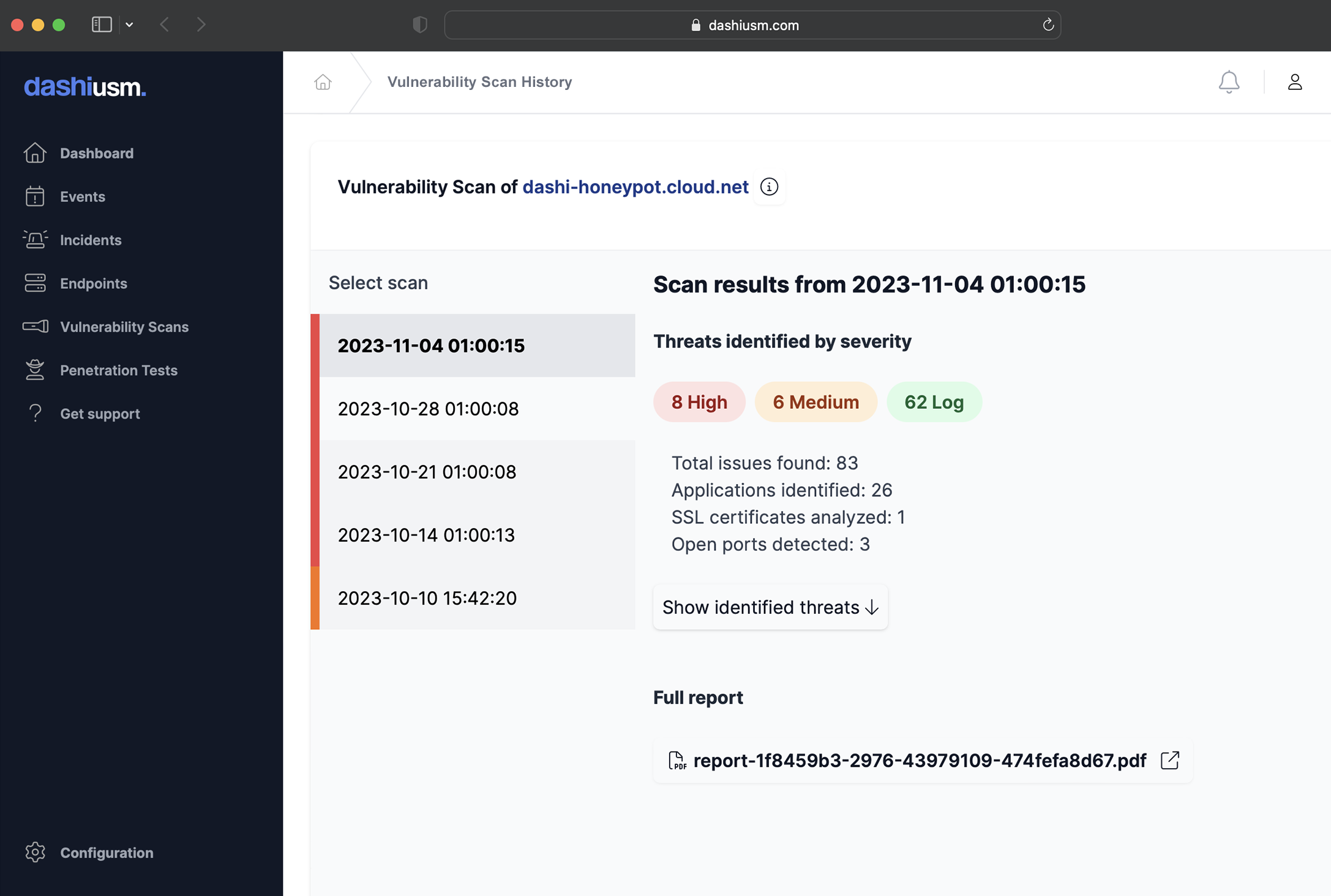
Scan for vulnerabilities
Fix your weaknesses before the bad guys find them
Scan your endpoints and websites with Dashi USM™ to identify weak security configurations, outdated software versions and common bugs and vulnerabilities. Detailed reports include suggested remediation procedures.
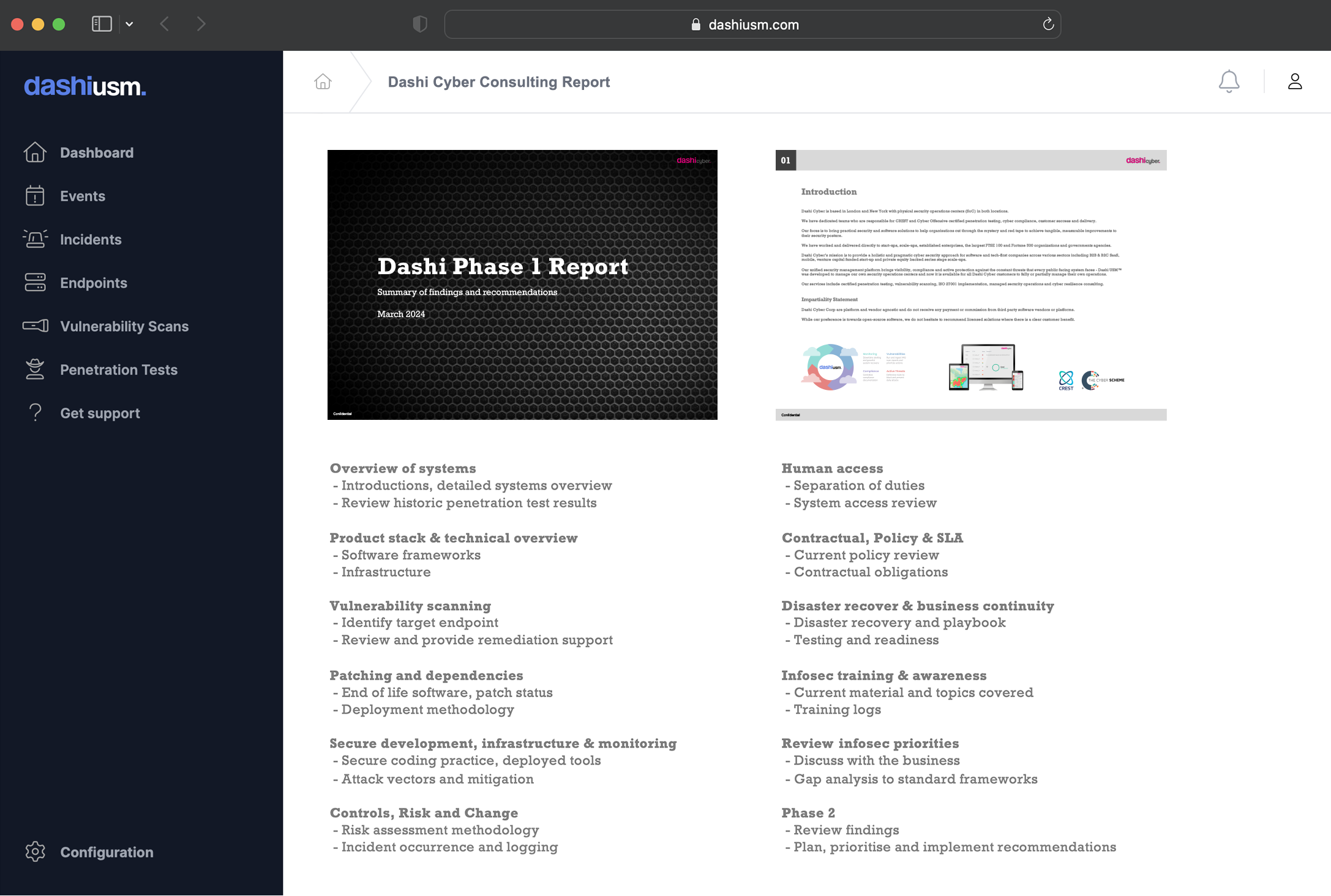
Exposure report
The Asset Exposure report really brings the whole system together
Get a close up view of how your information assets could be vulnerable to attack. Discover where your assets are stored and processed, what measures are in place to protect them, the risks involved, and what the consequences of a successful attack look like.
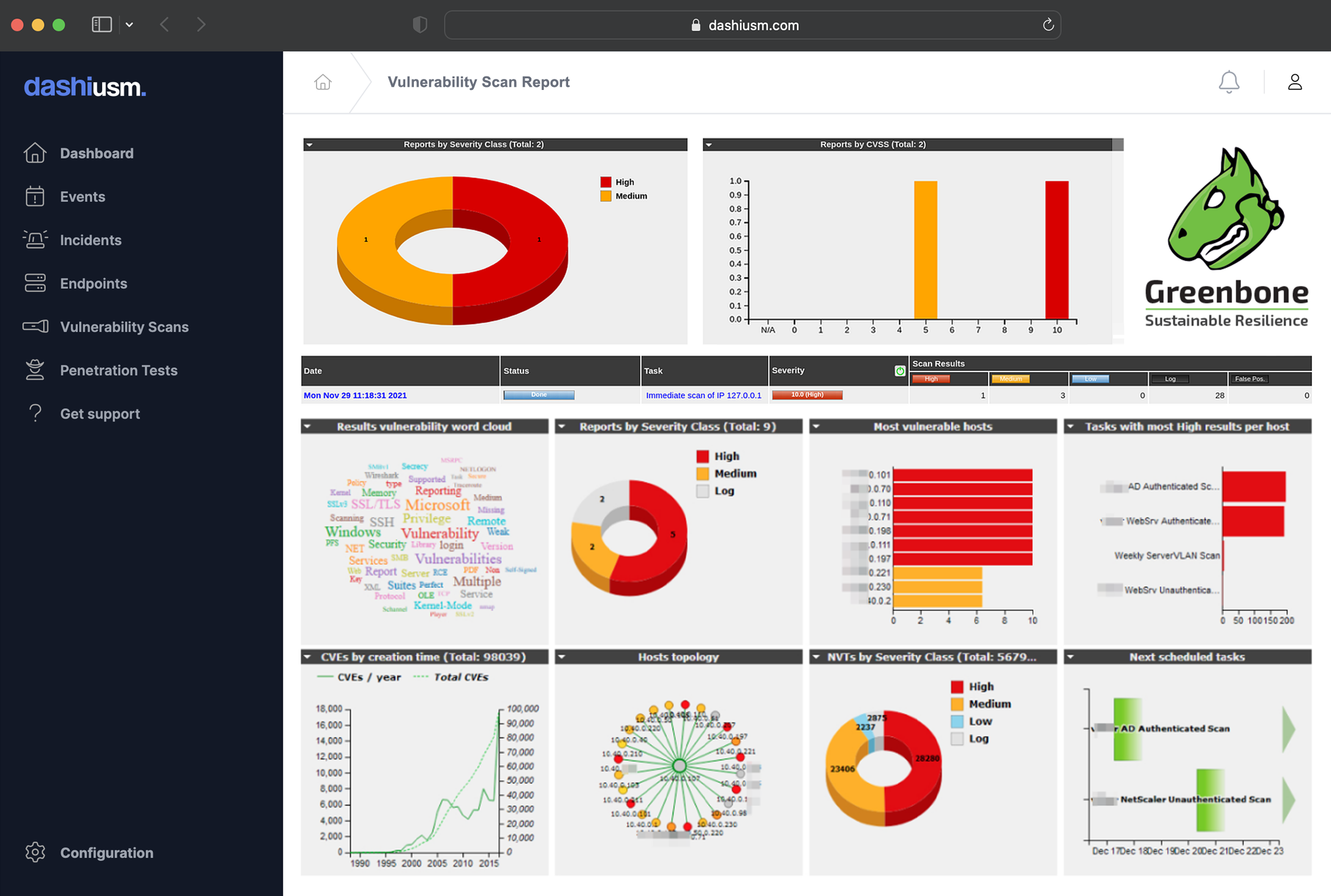
Know your attack surface
Dashi USM™ scans your endpoints for open ports and services. A dynamic port <-> endpoint map enables visualization of your network. Tabular views help identify ports that are open but should be closed. Alerts notify you every time a port is opened or closed, providing a key indicator of failed services or potential back doors.
Fix your weaknesses before the bad guys find them
Scan your endpoints and websites with Dashi USM™ to identify weak security configurations, outdated software versions and common bugs and vulnerabilities. Detailed reports include suggested remediation procedures.
The Asset Exposure report really brings the whole system together
Get a close up view of how your information assets could be vulnerable to attack. Discover where your assets are stored and processed, what measures are in place to protect them, the risks involved, and what the consequences of a successful attack look like.
Simple pricing
for additional features and services
Add all your endpoints for free, then upgrade only the ones you want to scan. Additional features and services are available.
FREE
Add all your endpoints for free.
$0
- Monitor your server and website availability
- Monitor for changes to open ports
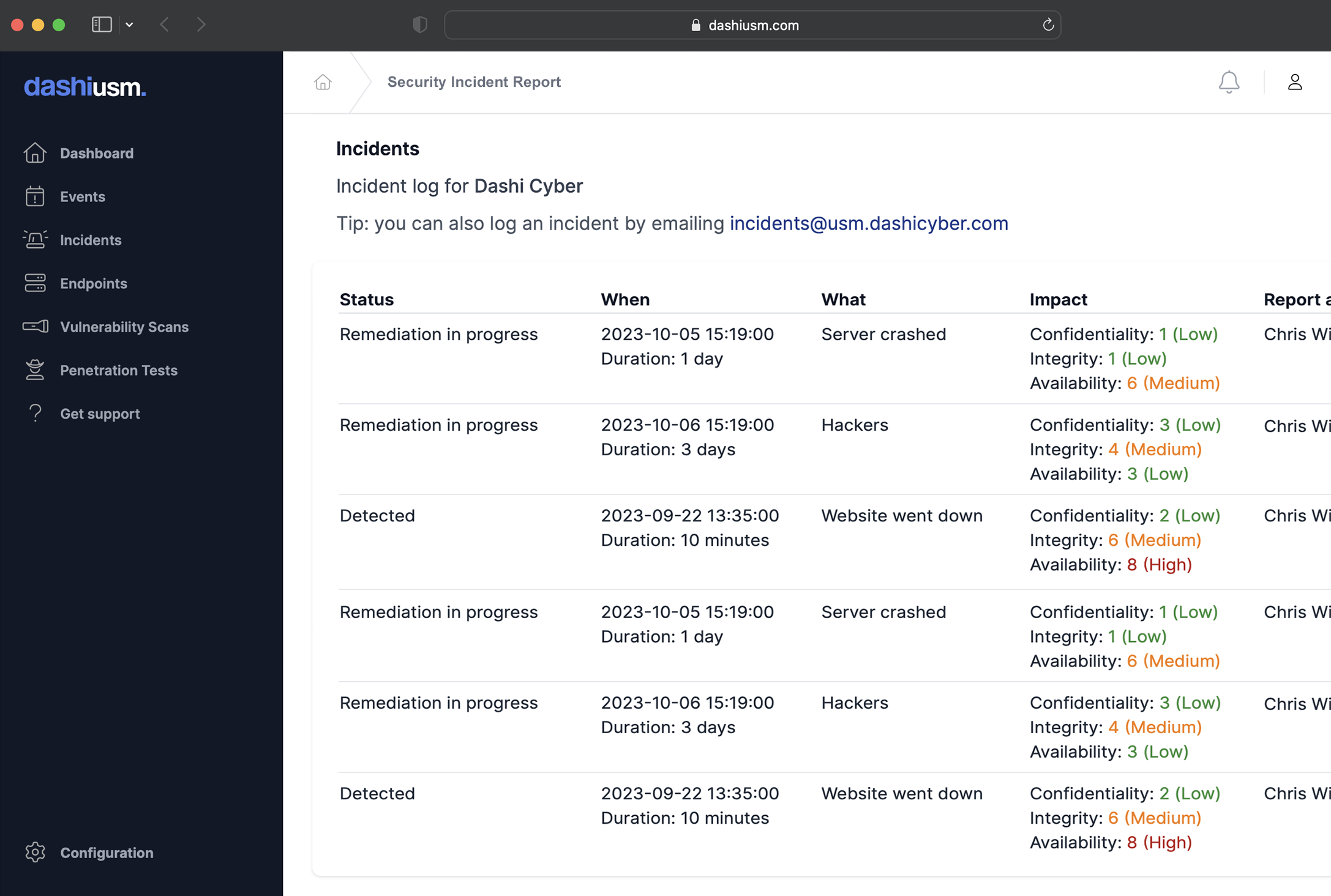
- Unify information security events by ingesting alerts from fail2ban, Nagios, or any other tool that can send a POST request or an email alert
- Log events and create detailed incident reports including event timelines, impact assessment, root cause analysis and remediation plans
- 30 day event log retention
Extended scanning
Enterprise grade security management.
$29/endpoint
- All features of the FREE plan
- Weekly enterprise grade vulnerability scanning to detect weaknesses in services, packages or configurations
- Remedial action suggestions to help you fix vulnerabilities
- 180 day event log retention
- Upgrade only the endpoints you want to scan
- No commitment, cancel anytime
Tough as nails
For your most critical endpoints.
$79/endpoint
- Everything in the FREE and Extended Scanning plans
- Daily enterprise grade vulnerability scanning to detect weaknesses in services, packages or configurations
- 7 year event log retention
- Direct access to our experienced sys admin team to guide you with vulnerability mitigation and security best practices
Website Security Scan
Comprehensive security scan for your website to detect security issues.
Our expert team will configure a scan profile based on your website's technology stack. The scanner then crawls your website and reports on security issues such as cross-site scripting vulnerabilities, SQL injection flaws, insecure cookies and more.
A comprehensive report and a 30 minute follow up consultation is included.
$199
- Best of breed scanning technology
- Authenticated and unauthenticated scans
- Advise on remediation of findings
- Tell us what to scan and we'll do the heavy lifting
- Reports saved in Dashi USM™
- No subscription required, scan on your own schedule
Management System
Build an ISO 27001 aligned information security management system directly in USM.
USM ISMS automatically links to your event and incident logs and asset inventory. No more manual entry and cross-referencing spreadsheets.
Templates are included for all parts of the management system.
$149/month
- Risk register: document risks and remediation plans
- Policy manager: write, maintain and track user acceptance
- Controls (Statement of Applicability): define the measures you put in place to protect your information assets
- Attributes: tailor controls to your organization and facilitate analysis of controls from varying angles
- Enforcements: define the mechanisms by which your organization is compelled to protect information
- Classifications: define types of information to help you categorize and prioritize the protection of information assets
All prices in USD, per month and exclusive of any applicable taxes.
Contact us for more information.
Frequently asked questions
Do you have a question that isn't answered here? Get in touch and we'll be happy to answer it for you.
What is an endpoint?
Any device that stores or processes confidential information should be added as an endpoint. Servers, laptops, mobile devices and cloud providers are all examples of endpoints.
Can I pay for my subscription via purchase order?
Enterprise customers who wish to pay annually may purchase via purchase order.
Do you offer ISO 27001 certification?
Our software will help you create the information security management structure you need for ISO 27001 compliance. We work closely with partners who can help you achieve certification.
Can you guarantee I won't get hacked?
We do our best to help you discover vulnerabilities before they can be exploited. As much as we would like to be able to guarantee 100% effectiveness that would simply not be possible. Proper implementation and ongoing maintenance of a well designed information security management system is the best way to protect your organization.
What do I need to get started?
A desire to improve your security posture. An hour or two to explore USM and start scanning your endpoints. That’s it.
What makes Dashi unique?
Our combination of software + people. We don't expect you to be able to build an effective information security management system without any experience. That's why we're here to help you every step of the way.
How will I know if I'm doing it right?
USM will notify you of any issues that need your attention. As you add more endpoints and data ingestion sources, your dashboard will start to show you a more complete picture of your security posture.
Do you have feature X?
If you need a feature we don't have yet please get in touch and tell us about it. We want to build software that works for you!
I lost my password, how do I get into my account?
Go to the sign in page then click Forgot Password.
I need vulnerability scanning. Do I need to pay for all my endpoints?
Upgrade only those endpoints you need to scan. You can upgrade and downgrade at any time.
Get started today
There's no better time to start securing your Internet facing systems. Sign up for free and start scanning your endpoints today. If you need help, we're here for you. You can contact us directly from the USM app.
Sign up for freePartner with us
Calling all ISO 27001 auditors, pen testers, security consultants, managed security service providers. Do you want to help businesses improve their information security posture, train their teams, and support them at every step along the way? Our partners are independent consultants, penetration testers and security consulting practices looking to retain, engage and grow their customer base and revenues by partnering with Dashi USM™. Register for your unique partner code for attractive partner benefits that will supercharge your business.
Contact us to enquire about joining our partner program.
What makes Dashi USM™ different?
Our early experience with consultants and template driven ISO 27001 systems left us feeling like the whole endeavor was an expensive box-ticking exercise that had to be done if we wanted the certification (which we needed) but provided little to no tangible benefit. We thought that was a real shame, because we could see how well considered and mature the standard is.
After throwing out the templates and completely rebuilding our information security management system from scratch, we quickly started to appreciate how the system helped us look at our setup from new angles and identify areas that needed improvement. Year after year our auditors passed us without finding any non-conformities. We thought others might benefit from the our experience, and Dashi Cyber was born.
Our goal is to help our customers build a beautiful, simple, practical management system that not only satisfies the requirements of the ISO 27001 standard, but also provides tangible results that directly improve the security of their organization.
In order to accomplish this goal, we came to the conclusion that security operations must be engaged and integrated into the management system. This brings awareness, understanding and improved communication, resulting in measurable and continuous improvement. This is fundamental to the whole raison d’etre of ISO 27001: to systematically improve security.